Enumeration:
Nmap
$ nmap -T4 -v -A 10.10.214.134 Nmap scan report for 10.10.214.134 Host is up (0.16s latency). Not shown: 999 closed ports PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) |_http-generator: WordPress 4.1.31 | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: ColddBox | One more machine
Nmap found only one port open i.e port 80.
Manual Website Inspection
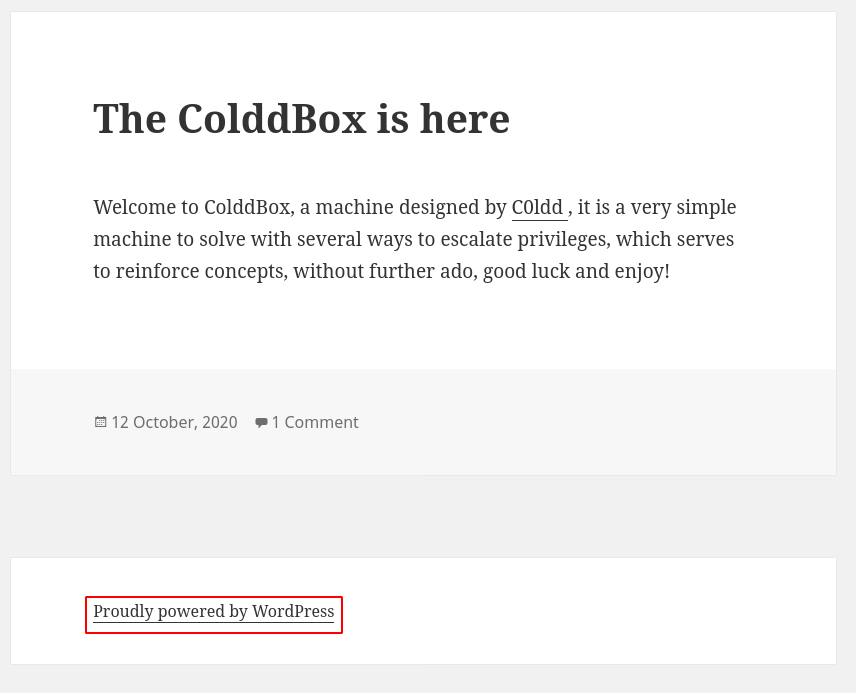
So it is a WordPress site. Let's enumerate more.
Gobuster
$ gobuster dir -u http://10.10.214.134 -w /opt/dirbuster/directory-list-2.3-medium.txt -t 20
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://10.10.214.134
[+] Method: GET
[+] Threads: 20
[+] Wordlist: /opt/dirbuster/directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.1.0
[+] Timeout: 10s
===============================================================
2021/01/07 12:58:08 Starting gobuster in directory enumeration mode
===============================================================
/wp-content (Status: 301)
/wp-includes (Status: 301)
/wp-admin (Status: 301)
/hidden (Status: 301)
Progress: 15900 / 220561 (7.21%)^C
[!] Keyboard interrupt detected, terminating.
===============================================================
2021/01/07 13:00:31 Finished
===============================================================
Bruteforcing directories with gobuster, finds a directory "hidden".
Navigating to that directory in the browser gives a hint on possible usernames.
WPscan
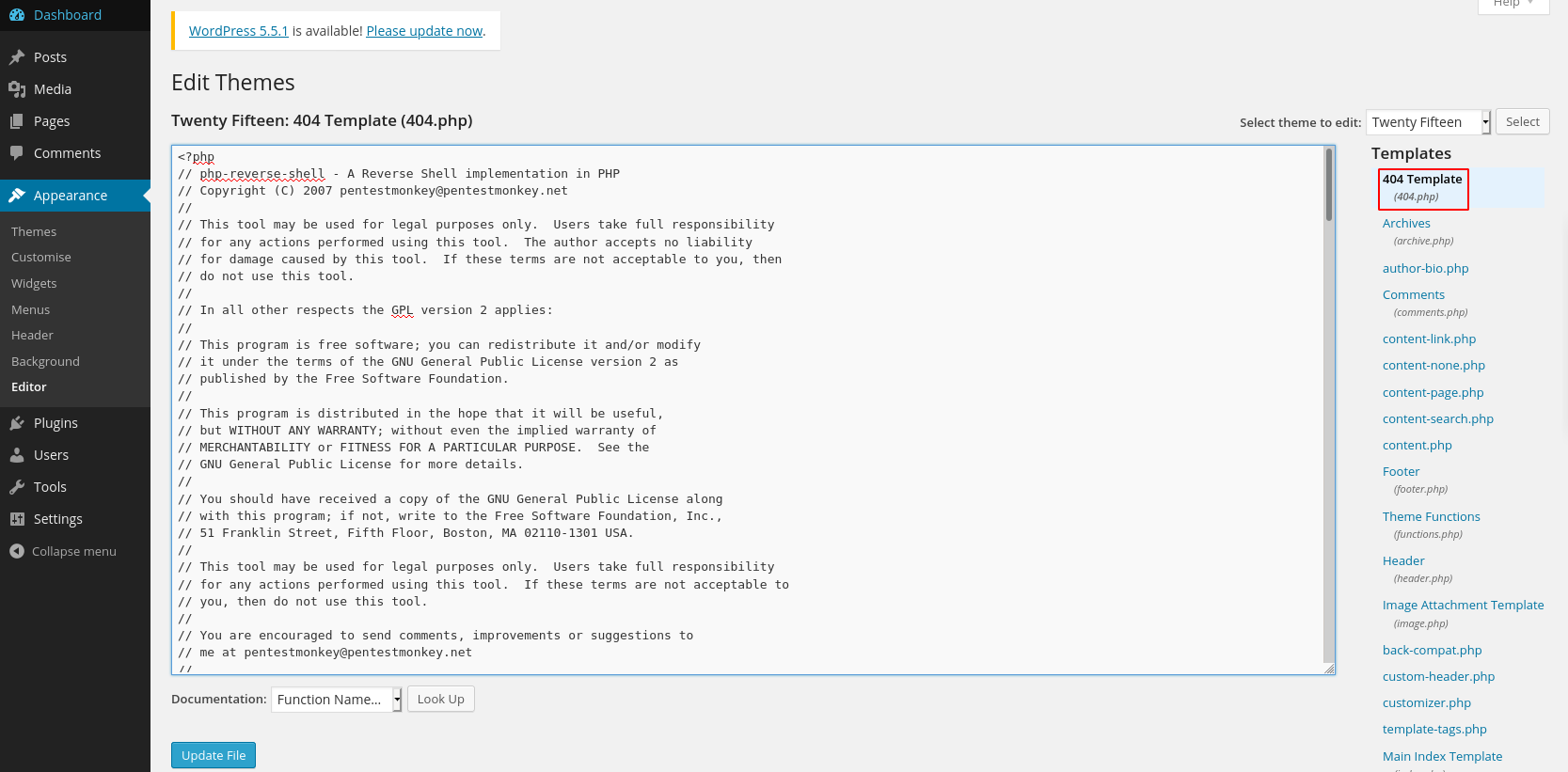
$ wpscan --no-banner --url http://10.10.214.134 -e u [+] URL: http://10.10.214.134/ [10.10.214.134] --snip-- [+] WordPress theme in use: twentyfifteen | Location: http://10.10.214.134/wp-content/themes/twentyfifteen/ | Last Updated: 2020-12-09T00:00:00.000Z | Readme: http://10.10.214.134/wp-content/themes/twentyfifteen/readme.txt | [!] The version is out of date, the latest version is 2.8 | Style URL: http://10.10.214.134/wp-content/themes/twentyfifteen/style.css?ver=4.1.31 | Style Name: Twenty Fifteen | Style URI: https://wordpress.org/themes/twentyfifteen | Description: Our 2015 default theme is clean, blog-focused, and designed for clarity. Twenty Fifteen's simple, st... | Author: the WordPress team | Author URI: https://wordpress.org/ | | Found By: Css Style In Homepage (Passive Detection) | | Version: 1.0 (80% confidence) | Found By: Style (Passive Detection) | - http://10.10.214.134/wp-content/themes/twentyfifteen/style.css?ver=4.1.31, Match: 'Version: 1.0' [+] Enumerating Users (via Passive and Aggressive Methods) --snip-- [i] User(s) Identified: [+] the cold in person | Found By: Rss Generator (Passive Detection) [+] hugo | Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Confirmed By: Login Error Messages (Aggressive Detection) [+] c0ldd | Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Confirmed By: Login Error Messages (Aggressive Detection) [+] philip | Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Confirmed By: Login Error Messages (Aggressive Detection)
It's long output from wpscan but there are two important things to observe, the theme used and the users identified.
If you google for "twentyfifteen" exploit you get a XSS Vulnerability. This doesn't help.