Enumeration:
Nmap
# Nmap 7.92 scan initiated Sun Apr 17 14:41:24 2022 as: nmap -v -T4 -A -oN nmap.results 10.10.141.251 Nmap scan report for 10.10.141.251 Host is up (0.28s latency). Not shown: 989 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 10:8a:f5:72:d7:f9:7e:14:a5:c5:4f:9e:97:8b:3d:58 (RSA) | 256 7f:10:f5:57:41:3c:71:db:b5:5b:db:75:c9:76:30:5c (ECDSA) |_ 256 6b:4c:23:50:6f:36:00:7c:a6:7c:11:73:c1:a8:60:0c (ED25519) 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) |_http-title: Apache2 Ubuntu Default Page: It works | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS |_http-server-header: Apache/2.4.18 (Ubuntu) 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP) 1010/tcp filtered surf 3998/tcp filtered dnx 6565/tcp filtered unknown 8099/tcp filtered unknown 9503/tcp filtered unknown 32782/tcp filtered unknown 62078/tcp filtered iphone-sync Service Info: Host: TECHSUPPORT; OS: Linux; CPE: cpe:/o:linux:linux_kernel Host script results: | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) | smb2-time: | date: 2022-04-17T09:12:04 |_ start_date: N/A | smb2-security-mode: | 3.1.1: |_ Message signing enabled but not required | smb-os-discovery: | OS: Windows 6.1 (Samba 4.3.11-Ubuntu) | Computer name: techsupport | NetBIOS computer name: TECHSUPPORT\x00 | Domain name: \x00 | FQDN: techsupport |_ System time: 2022-04-17T14:42:02+05:30 |_clock-skew: mean: -1h49m57s, deviation: 3h10m31s, median: 1s Read data files from: /usr/bin/../share/nmap Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . # Nmap done at Sun Apr 17 14:42:12 2022 -- 1 IP address (1 host up) scanned in 48.00 seconds
Nmap found four ports open i.e port 22, port 80, port 139 & port 445.
Samba and http services are the interesting ones. Let's enumerate them more.
SMBClient
$ smbclient -L //10.10.141.251/
Can't load /etc/samba/smb.conf - run testparm to debug it
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
websvr Disk
IPC$ IPC IPC Service (TechSupport server (Samba, Ubuntu))
SMB1 disabled -- no workgroup available
There is a share called "websvr". Let's see what's there in this share.
$ smbclient //10.10.141.251/websvr
Can't load /etc/samba/smb.conf - run testparm to debug it
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat May 29 12:47:38 2021
.. D 0 Sat May 29 12:33:47 2021
enter.txt N 273 Sat May 29 12:47:38 2021
8460484 blocks of size 1024. 5693632 blocks available
There is file called "enter.txt". Let's download and check the contents of this file.
GOALS ===== 1)Make fake popup and host it online on Digital Ocean server 2)Fix subrion site, /subrion doesn't work, edit from panel 3)Edit wordpress website IMP === Subrion creds |->admin:7sKvntXdPEJaxazce9PXi24zaFrLiKWCk [cooked with magical formula] Wordpress creds |->
This seems like an encoded string "7sKvntXdPEJaxazce9PXi24zaFrLiKWCk", let's try to decode it in CyberChef.
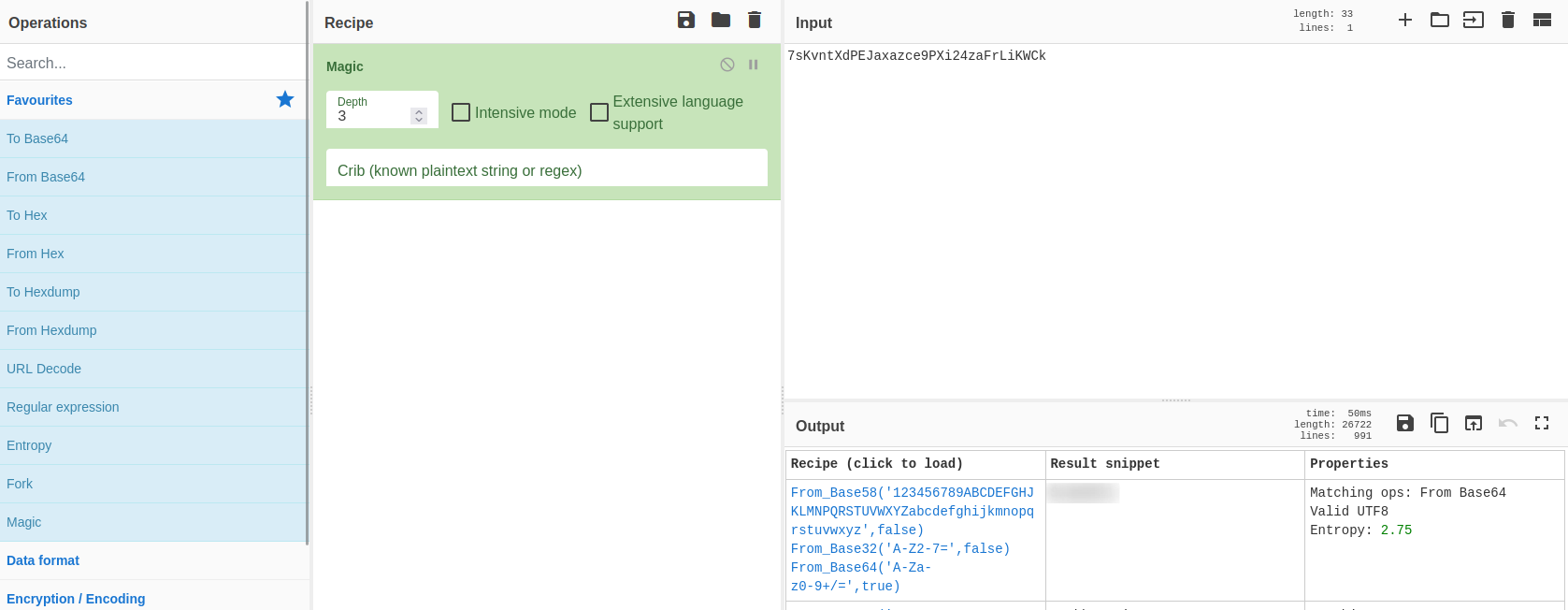
We'll get the credentials for Subrion CMS.
"admin:[redacted]"
Subrion
Visiting "/subrion", we'll get error. "enter.txt" says "edit from panel". The robots.txt from sbrion github repo has a directory "/panel"
So visiting "http://MACHINE-IP/subrion/panel" gives a login page.